 Windows Security Log Event ID 4717
Windows Security Log Event ID 4717

| Operating Systems |
Windows 2008 R2 and 7
Windows 2012 R2 and 8.1
Windows 2016 and 10
Windows Server 2019 and 2022
|
Category
• Subcategory | Policy Change
• Authentication Policy Change |
|
Type
|
Success
|
Corresponding events
in Windows
2003
and before |
621
|
4717: System security access was granted to an account
On this page
This event documents the grant of logon rights such as "Access this computer from the network" or "Logon as a service".
Rights, like most other security settings, are defined in group policy objects and applied by the computer. Therefore this event will normally show the Assigned By user as the system itself. To determine who actually made the rights assignment change you must search the domain controllers' security logs for changes to groupPolicyContainer objects (logged by Directory Service auditing). Logon ID allows you to link this event to the prior event 4624 logon event of the user who performed this action.
This event, 4717, documents the system name for each logon right as opposed to the more familiar description. Click here for a cross reference.
Note: This event and 4718 log changes to strictly logon rights such as "Access this computer from the network" or "Logon as a service" - not to other rights such as "Change the system time" or "Take ownership of files and other objects". See events 4704 and 4705.
Logon Rights
| System name |
Description |
| SeNetworkLogonRight |
Access this computer from the network |
| SeRemoteInteractiveLogonRight |
Allow logon through Terminal Services |
| SeDenyNetworkLogonRight |
Deny access to this computer from the network |
| SeDenyBatchLogonRight |
Deny logon as a batch job |
| SeDenyServiceLogonRight |
Deny logon as a service |
| SeDenyInteractiveLogonRight |
Deny logon locally |
| SeDenyRemoteInteractiveLogonRight |
Deny logon through Terminal Services |
| SeBatchLogonRight |
Log on as a batch job |
| SeServiceLogonRight |
Log on as a service |
| SeInteractiveLogonRight |
Log on locally |
Free Security Log Resources by Randy
Subject:
The ID and logon session of the user that changed the policy - always the local system - see note above.
- Security ID: The SID of the account.
- Account Name: The account logon name.
- Account Domain: The domain or - in the case of local accounts - computer name.
- Logon ID is a semi-unique (unique between reboots) number that identifies the logon session. Logon ID allows you to correlate backwards to the logon event (4624) as well as with other events logged during the same logon session.
Account Modified:
- Account Name: SID of the user/group/computer granted the logon right
Access Granted:
Supercharger Free Edition
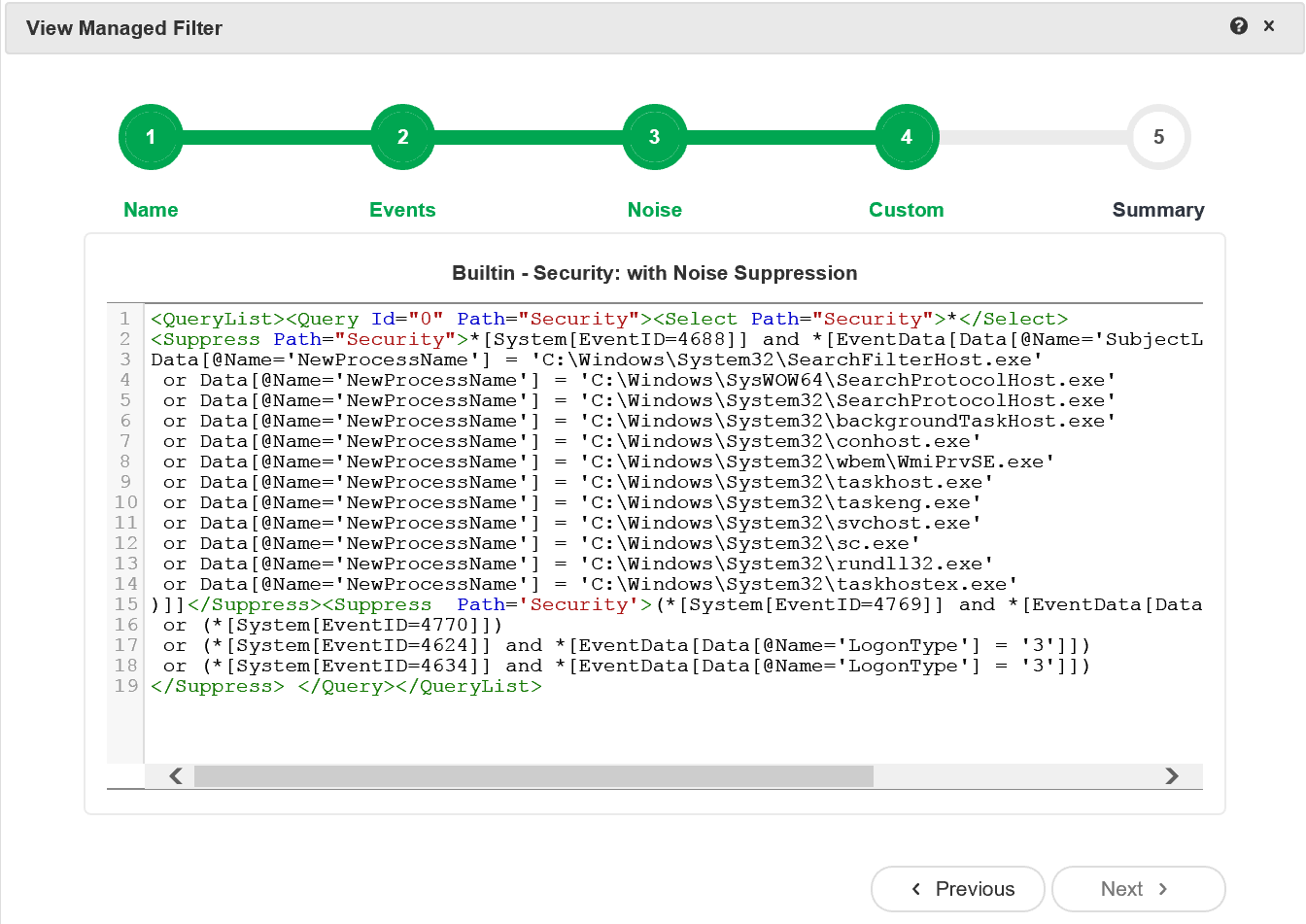
Supercharger's built-in Xpath filters leave the noise behind.
Free.