Chapter 6
Detailed Tracking Events
The Detailed Tracking category, which corresponds to the
Audit
process tracking events
policy setting, contains a number of subcategories listed in the chart below. However, the category’s primary purpose is to give you the
ability to track programs that are executed on the system and to link those
process events to logon sessions that are reported by Logon/Logoff events
(discussed in Chapter 5) and to file access events that are generated by the
Object Access category (discussed in Chapter 7).
|
Subcategories
|
Comment
|
|
Process Creation
|
New or child process
|
|
Process Termination
|
Process ending
|
|
DPAPI Activity
|
Data Protection API
|
|
RPC Events
|
Remote Procedure Call
|
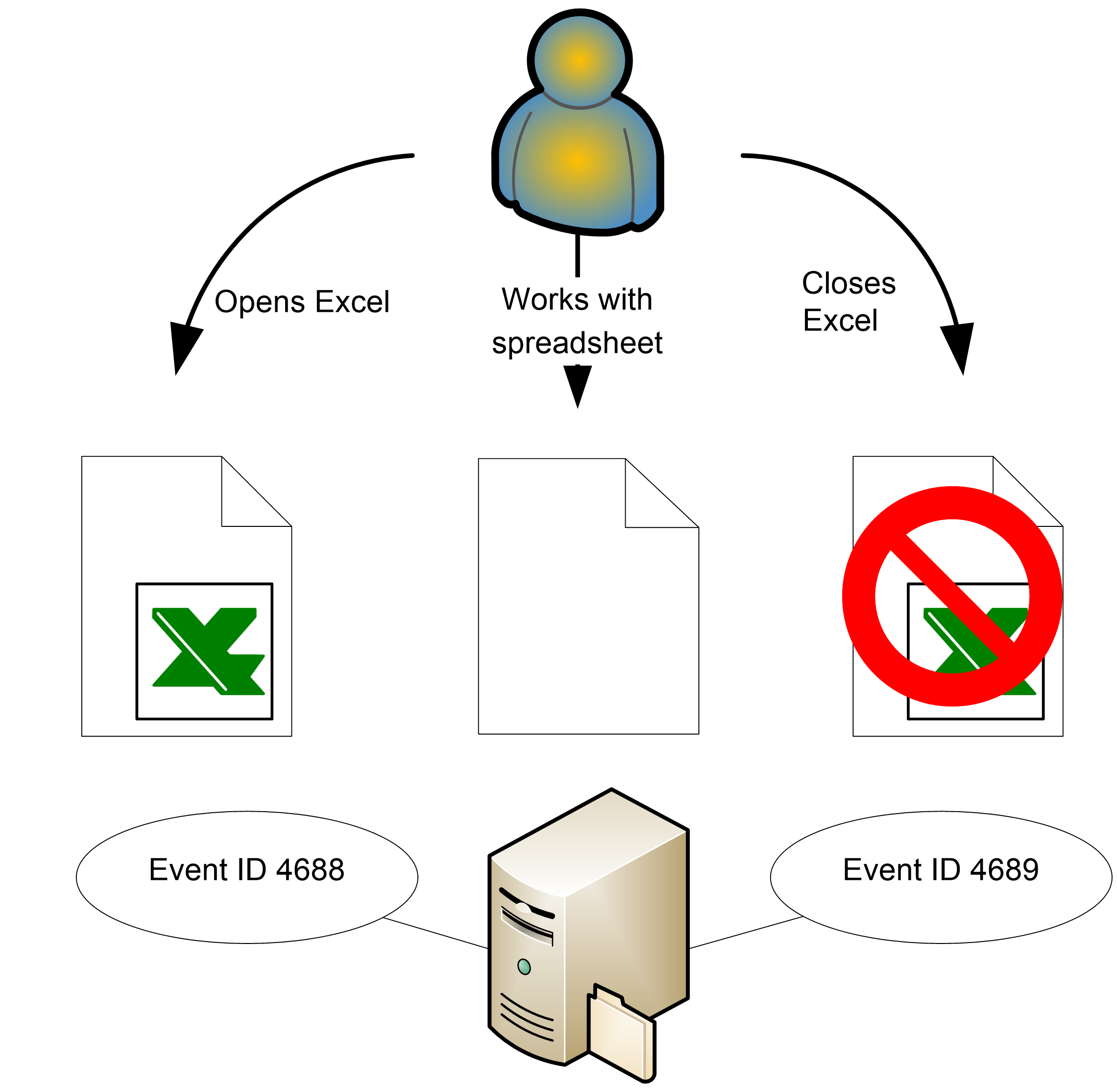
For instance, you can use Detailed Tracking events to
determine that Joe opened Excel as shown in the diagram below. By linking Detailed Tracking
events to Logon/Logoff events, you can further show that Joe opened Excel
during a Remote Desktop logon; by linking Detailed Tracking events to Object
Access events, you can document that Joe used Excel to open and modify the file
C:\files\payroll.xls.
Detailed Tracking also provides event IDs for monitoring
the installation and removal of services and the maintenance of scheduled
tasks. These events are handled by the Process Creation and Process Termination
subcategories. The other two subcategories, DPAPI Activity and RPC Events,
provide coverage of activity in the Data Protection Application Programming Interface
(DPAPI) and events that relate to Remote Procedure Calls (RPCs), which we’ll
discuss briefly later in this chapter.
Process Creation
The Process Creation subcategory provides just two event
IDs. When a system process or a user opens an executable, Windows
creates a process in which that executable runs and logs event ID 4688, which
identifies the executable and the account that started the process.
|
Event ID
|
Title
|
|
4688
|
A new process has been created
|
|
4696
|
A primary token was assigned to process
|
Event ID 4688 contains a New Process Name description
field, which identifies the full pathname of the executable that was started. For instance, if a user opens WordPad, the event will show something
similar to C:\Program Files\Windows NT\Accessories\wordpad.exe as the image
filename.
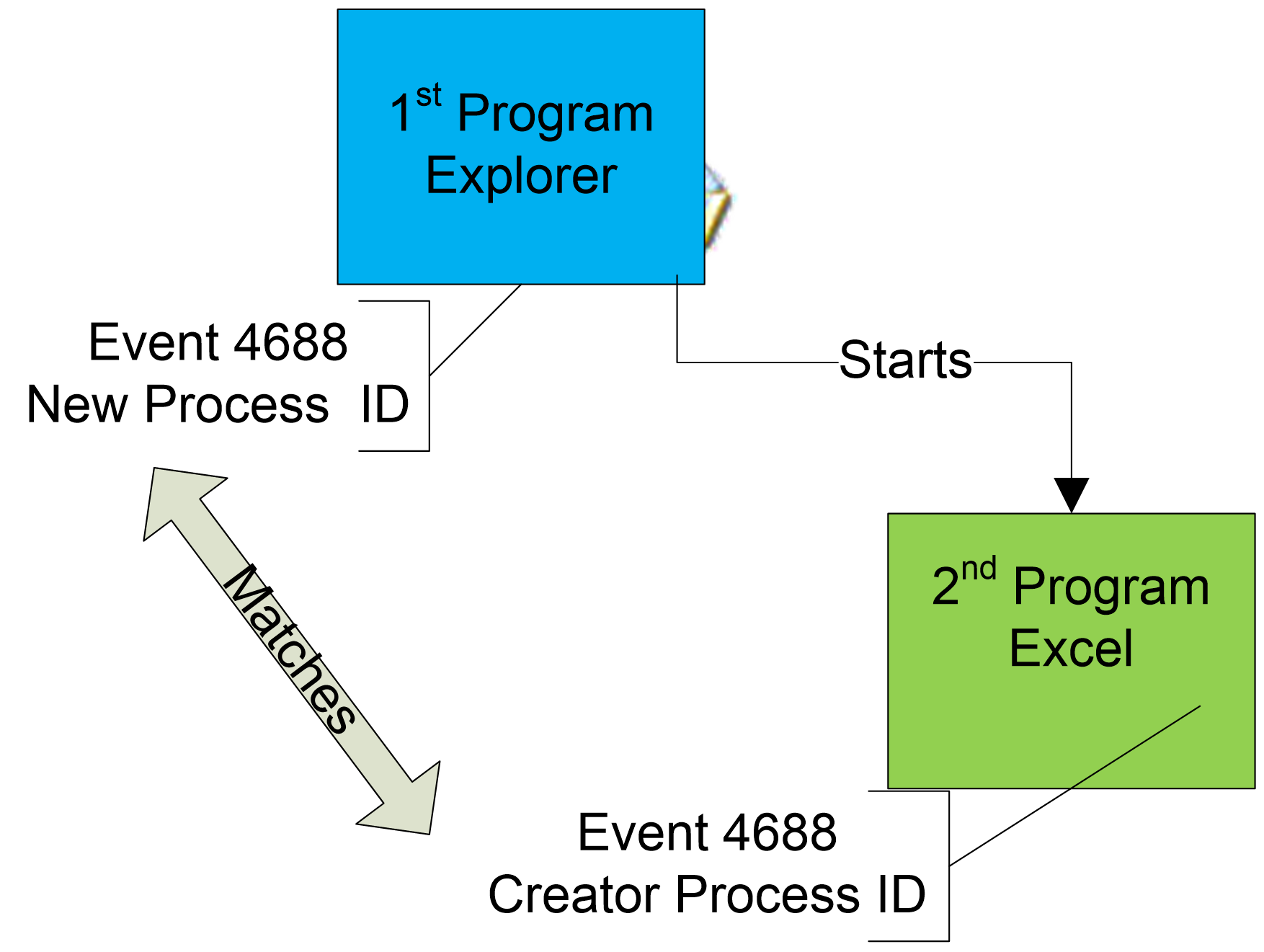
To uniquely identify each process during a system boot
session, Windows uses a Process ID, which you might have noticed when viewing
the Task Manager Processes tab. Event ID 4688 lists the ID of a new process in
the New Process ID description field and lists the ID of the process that
created the new process in the Creator Process ID description field. The Creator Process ID gives you more information about why and how the
program was started. For instance, programs that users open from the Start Menu
will list the creator process as the current ID of Explorer—the Windows
desktop. Processes that start as system services will list the ID of the service
control manager as the Creator Process ID.
Token Elevation Type is a new feature in the Windows
Server 2008 and later. In Windows Server 2008 and later, User
Account Control (UAC) is installed and enabled by default. UAC separates the
standard users credentials from administrator credentials. Security is enhanced
because the least privilege principle is used. Many tasks don’t require full
administrator privileges. So UAC places 10 Security Options under the Local
Security Policy. These options control if and when the token privilege is
elevated. When a process is created, event ID 4688 will indicate which Token
Elevation Type is in effect.
|
Token Elevation Type
|
Description
|
|
1
|
Default (full token as if no UAC)
|
|
2
|
Elevated (token with increased privilege)
|
|
3
|
Limited (token with decreased privilege)
|
In previous Windows versions, Type 1 (Default) was the
only option. You might get tired of the extra Token Elevation Type description
text that Microsoft now puts into these events, especially if you’re saving
event logs in text format. The XML portion (as described in Chapter 2) does not
contain this text.
You might see the other Process Creation event—event ID
4696 (A primary token was assigned to process)—when a service or a
scheduled task starts under a different user’s authority. This event has little
value; the important information is found in the other events.
Process Termination
When a process terminates, Windows logs event ID 4689. Event ID 4689 also lists the Process ID field in its description, so
you can link an instance of that event to the corresponding instance of event
ID 4688 and thus determine not just when a program started but when it stopped
as well.
|
Event ID
|
Title
|
|
4689
|
A process has exited
|
Linking Detailed Tracking Events with Logon/Logoff Events
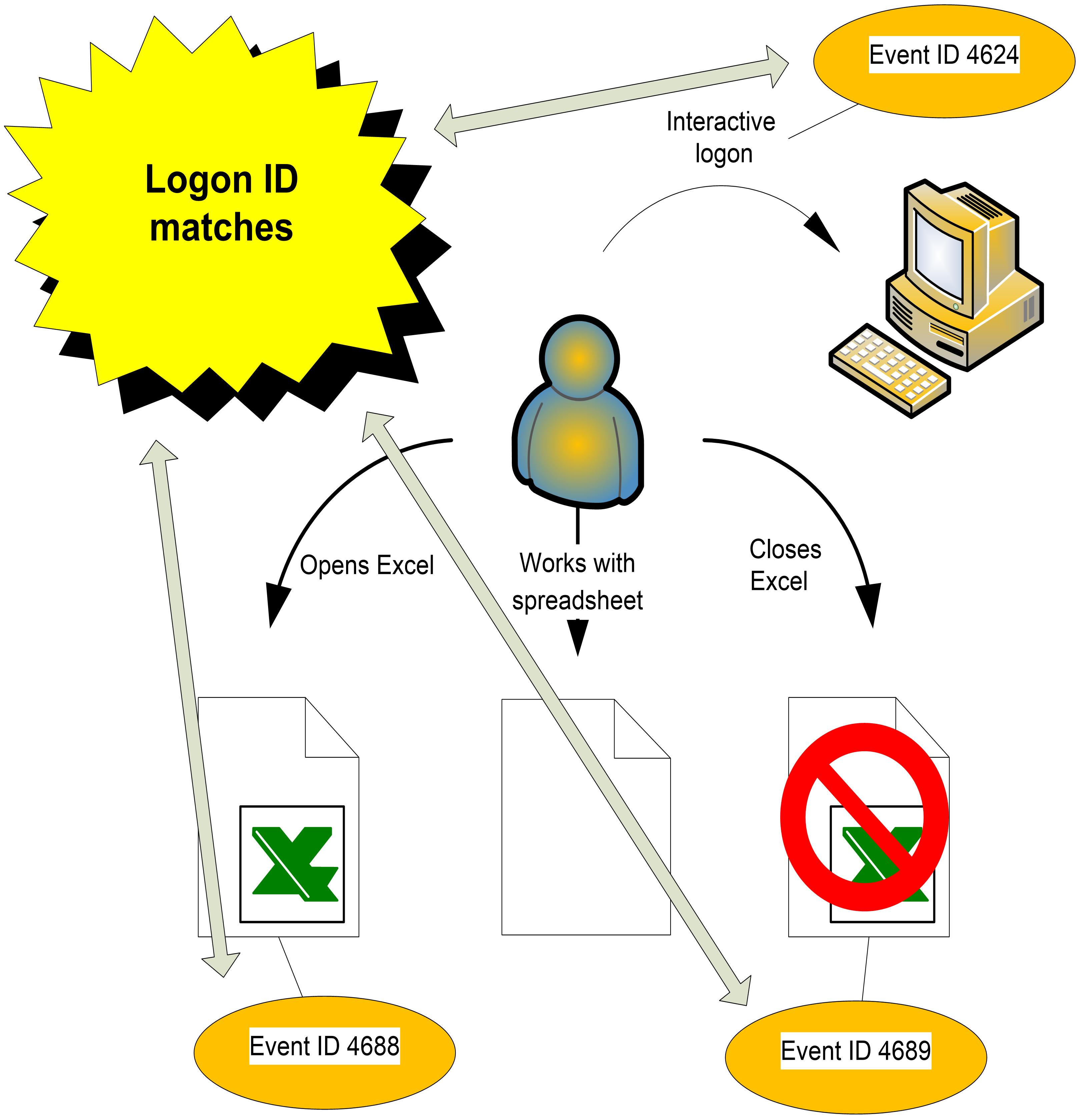
You’ll find process IDs in many other security events,
giving you the ability to determine the program and person that generated the
event. To determine the logon session during which a process
started, look at the Logon ID description field in event ID 4688, then find the
preceding event ID 4624 instance that has the same Logon ID. Check the Logon
Type and Logon Process fields to determine whether the process was started
during an interactive or Remote Desktop session (or some other type of logon
session).
DPAPI Activity
The DPAPI Activity subcategory reports activity concerning
the DPAPI. Per Microsoft: "The Data Protection API (DPAPI) helps to protect
data in Windows 2000 and later operating systems. DPAPI is used to help protect
private keys, stored credentials (in Windows XP and later), and other
confidential information that the operating system or a program wants to keep
confidential." We haven’t see a lot of the events in this subcategory, but examining a system that has been under attack might reveal them.
Event ID 4695 might indicate an attack, although you’ll also see this event
during normal activity. It could mean that a users password was changed and
attempts to decrypt with the new password failed. You will see this event if
another user attempts to decrypt information. You can find a more detailed
description of these events at www.ultimatewindowssecurity.com.
|
Event ID
|
Title
|
|
4692
|
Backup of data protection master key was attempted.
|
|
4693
|
Recovery of data protection master key was attempted.
|
|
4694
|
Protection of auditable protected data was attempted.
|
|
4695
|
Unprotection of auditable protected data was attempted.
|
RPC Events
According to the Windows manifest, the RPC
Events subcategory logs events that relate to RPC activity. However, at the time of this writing, we have not observed either of these
events.
|
Event ID
|
Title
|
|
4816
|
RPC detected an integrity violation while decrypting an incoming message.
|
|
5712
|
A Remote Procedure Call (RPC) was attempted.
|
Bottom Line
Detailed Tracking events can be effective auditing tools,
especially for forensic purposes. These events give you a full audit trail of
every program executed on a given computer. You might have noticed that some
events, such as scheduled task tracking events and events having to do with
object handles, are no longer listed under this category. Microsoft has moved
these events to the Object Access category.