 Windows Security Log Event ID 4768
Windows Security Log Event ID 4768

| Operating Systems |
Windows 2008 R2 and 7
Windows 2012 R2 and 8.1
Windows 2016 and 10
Windows Server 2019 and 2022
Windows Server 2025
|
Category
• Subcategory | Account Logon
• Kerberos Authentication Service |
|
Type
|
Success
Failure
|
Corresponding events
in Windows
2003
and before |
672
,
676
|
4768: A Kerberos authentication ticket (TGT) was requested
On this page
This event is logged on domain controllers only and both success and failure instances of this event are logged.
At the beginning of the day when a user sits down at his or her workstation and enters his domain username and password, the workstation contacts a local DC and requests a TGT. If the username and password are correct and the user account passes status and restriction checks, the DC grants the TGT and logs event ID 4768 (authentication ticket granted).
If the ticket request fails Windows will either log this event, 4768 or 4771 with failure as the type.
The User field for this event (and all other events in the Audit account logon event category) doesn't help you determine who the user was; the field always reads N/A. Rather look at the Account Information: fields, which identify the user who logged on and the user account's DNS suffix. The User ID field provides the SID of the account.
Windows logs other instances of event ID 4768 when a computer in the domain needs to authenticate to the DC typically when a workstation boots up or a server restarts. In these instances, you'll find a computer name in the User Name and fields. Computer generated kerberos events are always identifiable by the $ after the computer account's name.
Microsoft's Comments:
This event records that a Kerberos TGT was granted, actual access will not occur until a service ticket is granted, which is audited by Event 673. If the PATYPE is PKINIT, the logon was a smart card logon.
Result codes:
| Result code |
Kerberos RFC description |
Notes on common failure codes |
| 0x1 |
Client's entry in database has expired |
|
| 0x2 |
Server's entry in database has expired |
|
| 0x3 |
Requested protocol version # not supported |
|
| 0x4 |
Client's key encrypted in old master key |
|
| 0x5 |
Server's key encrypted in old master key |
|
| 0x6 |
Client not found in Kerberos database |
Bad user name, or new computer/user account has not replicated to DC yet |
| 0x7 |
Server not found in Kerberos database |
New computer account has not replicated yet or computer is pre-w2k |
| 0x8 |
Multiple principal entries in database |
|
| 0x9 |
The client or server has a null key |
administrator should reset the password on the account |
| 0xA |
Ticket not eligible for postdating |
|
| 0xB |
Requested start time is later than end time |
|
| 0xC |
KDC policy rejects request |
Workstation restriction, or Authentication Policy Silo (look for event ID 4820) |
| 0xD |
KDC cannot accommodate requested option |
|
| 0xE |
KDC has no support for encryption type |
|
| 0xF |
KDC has no support for checksum type |
|
| 0x10 |
KDC has no support for padata type |
|
| 0x11 |
KDC has no support for transited type |
|
| 0x12 |
Clients credentials have been revoked |
Account disabled, expired, locked out, logon hours. |
| 0x13 |
Credentials for server have been revoked |
|
| 0x14 |
TGT has been revoked |
|
| 0x15 |
Client not yet valid - try again later |
|
| 0x16 |
Server not yet valid - try again later |
|
| 0x17 |
Password has expired |
The user’s password has expired. |
| 0x18 |
Pre-authentication information was invalid |
Usually means bad password |
| 0x19 |
Additional pre-authentication required* |
|
| 0x1F |
Integrity check on decrypted field failed |
|
| 0x20 |
Ticket expired |
Frequently logged by computer accounts |
| 0x21 |
Ticket not yet valid |
|
| 0x21 |
Ticket not yet valid |
|
| 0x22 |
Request is a replay |
|
| 0x23 |
The ticket isn't for us |
|
| 0x24 |
Ticket and authenticator don't match |
|
| 0x25 |
Clock skew too great |
Workstation’s clock too far out of sync with the DC’s |
| 0x26 |
Incorrect net address |
IP address change? |
| 0x27 |
Protocol version mismatch |
|
| 0x28 |
Invalid msg type |
|
| 0x29 |
Message stream modified |
|
| 0x2A |
Message out of order |
|
| 0x2C |
Specified version of key is not available |
|
| 0x2D |
Service key not available |
|
| 0x2E |
Mutual authentication failed |
may be a memory allocation failure |
| 0x2F |
Incorrect message direction |
|
| 0x30 |
Alternative authentication method required* |
|
| 0x31 |
Incorrect sequence number in message |
|
| 0x32 |
Inappropriate type of checksum in message |
|
| 0x3C |
Generic error (description in e-text) |
|
| 0x3D |
Field is too long for this implementation |
|
Free Security Log Resources by Randy
Account Information:
- Account Name: logon name of the account that just authenticated
- Supplied Realm Name: domain name of the account
- User ID: SID of the account
- MSDS-SupportedEncryptionTypes:
- Available Keys:
Service Information:
- Service Name: always "krbtgt"
- Service ID:
- MSDS-SupportedEncryptionTypes:
- Available Keys:
Domain Controller Information:
- MSDS-SupportedEncryptionTypes:
- Available Keys:
Network Information:
- Client Address: IP address where user is present
- Client Port: source port
- Advertized Etypes:
Additional Information:
- Ticket Options: unknown. Please start a discussion if you have information to share on this field.
- Result Code: error if any - see above table
- Ticket Encryption Type: unknown. Please start a discussion if you have information to share on this field.
- Session Encryption Type:
- Pre-Authentication Type: unknown. Please start a discussion if you have information to share on this field.
- Pre-Authentication EncryptionType:
Certificate Information:
This information is only filled in if logging on with a smart card.
- Certificate Issuer Name:
- Certificate Serial Number:
- Certificate Thumbprint:
Ticket Information:
- Response ticket hash: Unique identifier of the ticket issuedy by the domain controller which can be either a ticket granting ticket (event id 4768) or a ticket granting service (event id 4769 and 4770)
Supercharger Free Edition
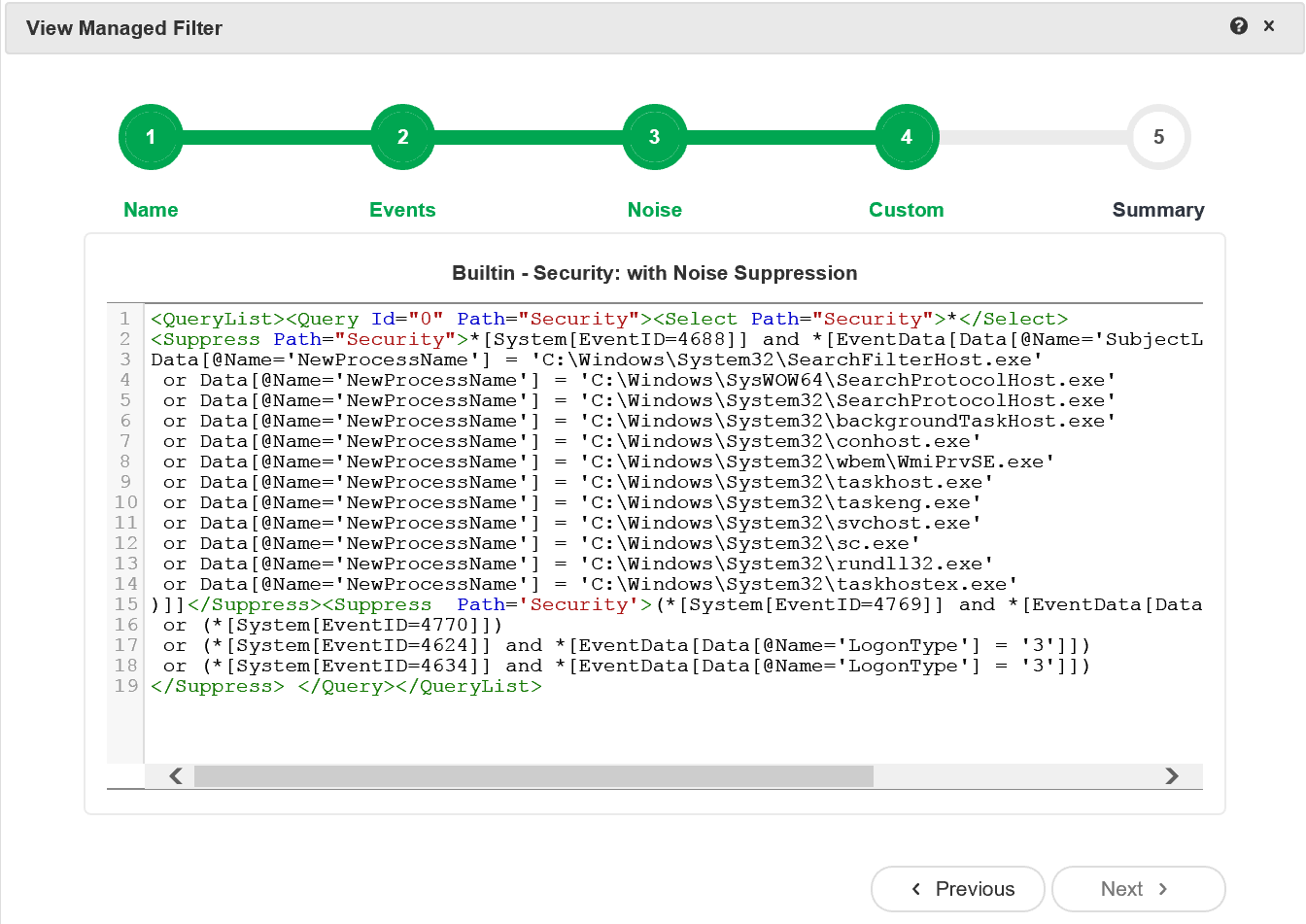
Supercharger's built-in Xpath filters leave the noise behind.
Free.
Success
A Kerberos authentication ticket (TGT) was requested.
Account Information:
Account Name: Administrator
Supplied Realm Name: acme-fr
User ID: ACME-FR\administrator
MSDS-SupportedEncryptionTypes:
Available Keys:
Service Information:
Service Name: krbtgt
Service ID: ACME-FR\krbtgt
MSDS-SupportedEncryptionTypes:
Available Keys:
Domain Controller Information:
MSDS-SupportedEncryptionTypes:
Available Keys:
Network Information:
Client Address: ::1
Client Port: 0
Advertized Etypes:
Additional Information:
Ticket Options: 0x40810010
Result Code: 0x0
Ticket Encryption Type: 0x12
Session Encryption Type:
Pre-Authentication Type: 2
Pre-Authentication EncryptionType:
Certificate Information:
Certificate Issuer Name:
Certificate Serial Number:
Certificate Thumbprint:
Ticket Information:
Response Ticket Hash:
Certificate information is only provided if a certificate was used for pre-authentication.
Pre-authentication types, ticket options, encryption types and result codes are defined in RFC 4120.
Failure
A Kerberos authentication ticket (TGT) was requested.
Account Information:
Account Name: nebuchadnezzar
Supplied Realm Name: acme-fr
User ID: NULL SID
MSDS-SupportedEncryptionTypes:
Available Keys:
Service Information:
Service Name: krbtgt/acme-fr
Service ID: NULL SID
MSDS-SupportedEncryptionTypes:
Available Keys:
Domain Controller Information:
MSDS-SupportedEncryptionTypes:
Available Keys:
Network Information:
Client Address: ::1
Client Port: 0
Advertized Etypes:
Additional Information:
Ticket Options: 0x40810010
Result Code: 0x12
Ticket Encryption Type: 0xffffffff
Session Encryption Type:
Pre-Authentication Type: -
Pre-Authentication EncryptionType:
Certificate Information:
Certificate Issuer Name:
Certificate Serial Number:
Certificate Thumbprint:
Ticket Information:
Response Ticket Hash:
Certificate information is only provided if a certificate was used for pre-authentication.
Pre-authentication types, ticket options, encryption types and result codes are defined in RFC 4120. EditMore Resources
Top 10 Windows Security Events to Monitor
Free Tool for Windows Event Collection