Every year, organizations spend millions of frustrating hours and countless sums of money trying to reverse the damage done by malware attacks. The harm caused by malware can be astronomical, going well beyond intellectual property loss and huge fines levied for non-compliance. In 2014, the cost of malware attacks and resulting breaches was estimated at $491 billion. [i] And these costs include more than just the money spent trying to directly respond to security breaches. Productivity, long-term profitability, and brand reputation are often severely impacted as well.
The malware threat is growing larger and becoming more challenging to respond to every year.  It seems like every month there are more major breaches. Target, Neiman Marcus, and UPS have all been victims of costly breaches in the past couple years, with each event showing signs that the breaches could have been prevented. Phishing-based malware was the starting point 95 percent of the time in state-sponsored attacks, and 67 percent of the time in cyber-espionage attacks.[ii]
It seems like every month there are more major breaches. Target, Neiman Marcus, and UPS have all been victims of costly breaches in the past couple years, with each event showing signs that the breaches could have been prevented. Phishing-based malware was the starting point 95 percent of the time in state-sponsored attacks, and 67 percent of the time in cyber-espionage attacks.[ii]
With such high-profile organizations being the target of attacks, do you really need to be worried?
CAN IT HAPPEN TO YOU?
It’s easy to shrug off the threat of malware and believe that the target will always be a retail organization or a huge brand name, that it will never be your organization. However, according to a 2015 Ponemon study, 80 percent of all organizations experience some form of Web-borne malware. [iii] So don’t be lulled into a false sense of security: All industries are at risk, including the financial, health care, and government sectors you hear about in the news.

And remember, these attacks aren’t confined to large, multinational corporations. Cybercriminals frequently target small and midsized businesses (SMBs). A prime example of an attack on a small business is Pennsylvania-based 80sTees.com. A cyberattack occurred in 2014, costing the company $200,000, not including lost sales after the attack while the company had to temporarily stop accepting credit card payments. Granted, this attack is not on the same scale from a total dollar perspective as the more well-publicized breaches we hear about in the media. But for a small company, an attack of this size can be just as devastating, if not more so.
Malware is not just an annoyance or minor inconvenience. It is the gateway to far more serious problems for a company and its customers. And it invades a network easily. There are many insidious ways it can infect a system email attachments, phishing email messages, various file-sharing programs, and out-of-date OS patching, to name a few. And once it affects a single computer or network node, it can quickly spread throughout your network like an out-of-control forest fire. This is called a horizontal kill chain and features heavily in every attack we analyze.
TAKING ACTION
What if there were a way to solve these potentially devastating problems before they got out of hand? Or even before they occurred in the first place? There is. This paper discusses just such a real-life situation, in which a malware attack took place but was discovered by the built-in rules of LogRhythm before any damage occurred.
The situation involves a customer of LogRhythm. LogRhythm is a leading provider of security intelligence and analytics solutions. LogRhythm empowers organizations around the globe to rapidly detect, respond to, and neutralize damaging cyber threats, giving clients the ability to catch and proactively solve problems they might not have otherwise anticipated.
What follows is a textbook example of the kind of problems LogRhythm solves on a regular basis and the risks it mitigates for its customers every day. This malicious activity could have led to a very serious intrusion with devastating repercussions, but LogRhythm caught it immediately and the client was able to research and mitigate it easily and quickly by using additional capabilities of LogRhythm including packet analysis, custom alarms and more.
THE HACK FOUND
It all started when the organization received a SIEM alarm from LogRhythm’s Advanced Intelligence Engine (AIE), notifying the IT team of a suspicious situation: A single domain user account had established simultaneous VPN access from two separate locations. This anomaly was caught because of a default, out of the box rule in LogRhythm as shown in Figure 1.
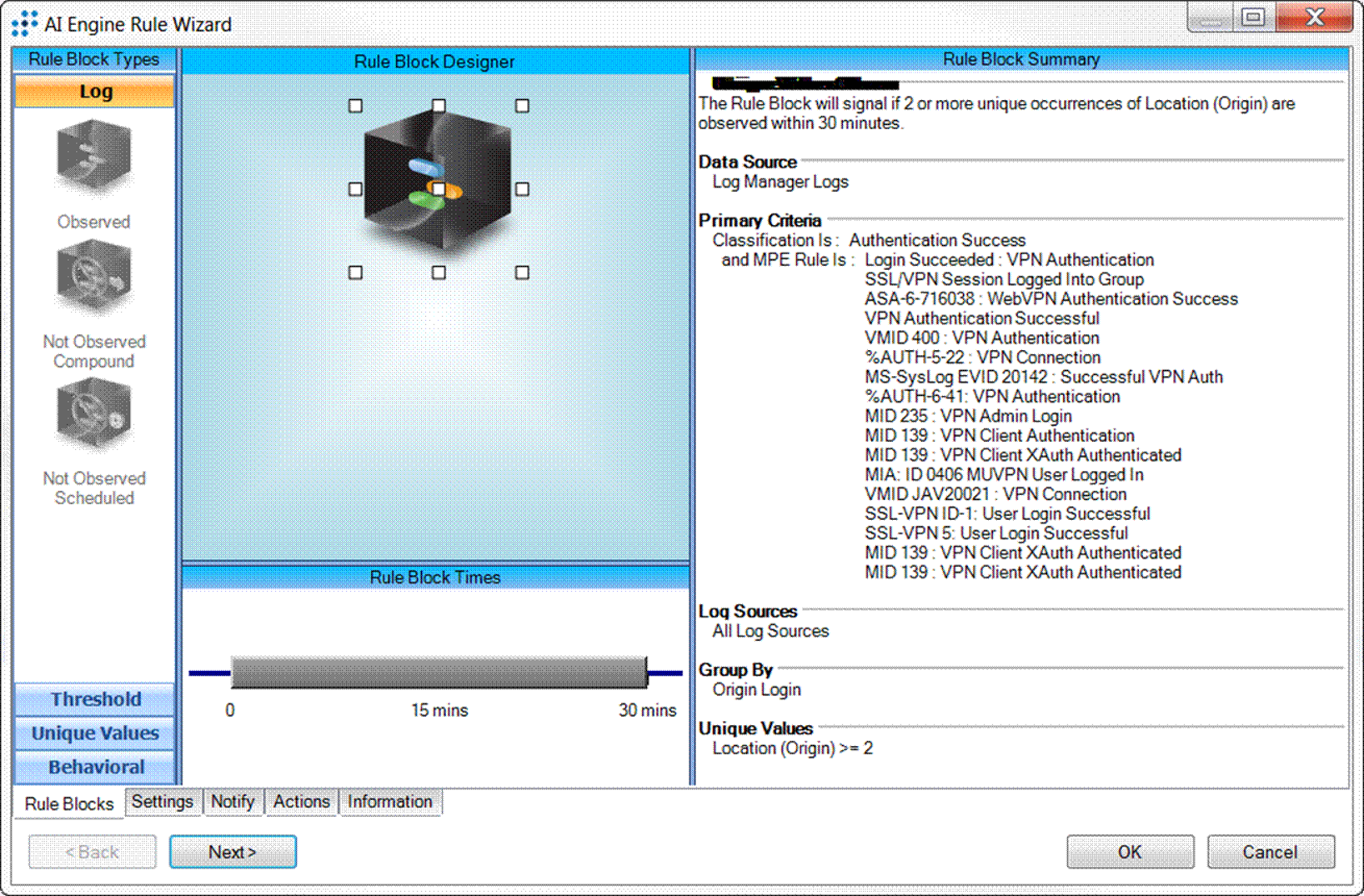
Figure 1: LogRhythm's AI Engine
The situation was an obvious case of compromised user credentials. A corporate end user should typically not be logging in simultaneously from two geographically separate locations. In response, the organization’s Security Operations Center (SOC) called the end user (who happened to be a technical security staff member himself) to investigate the matter. The SOC wondered if the user had set up a proxy device from home, or was perhaps using his mobile device to initiate a connection or even running his own penetration test just to play with his colleagues. The SOC determined that the end user had no malicious intent; he was using the VPN in a legitimate fashion while traveling on a business trip.
Because he was boarding a return flight soon and would not need his laptop, the SOC instructed the user to turn it off until he arrived back at the home office and could deliver it to the investigation team. Additionally, the SOC disabled the compromised Active Directory account, and the user’s computer account was removed from the network.
THE HACK ISOLATED
Once the laptop was received, IT ran a full antivirus scan and found no suspicious files or programs on the system. The IT team then placed the unit in an isolation/test lab for observation before reimaging it, because they wanted to identify the source of the problem and take steps to prevent it in the future. So, the computer was isolated and observed with LogRhythm’s network monitoring probe running.
At many organization management frequently over-relies on antivirus and assumes the organization is protected from any sort of malware damage. This is a serious misconception.
This particular threat was polymorphic in nature and as the name implies, it has the ability to change or “morph” regularly, thereby altering the appearance of its code. This characteristic bypasses detection by traditional antivirus tools and signatures. In our scenario, a more advanced scanner was deployed, and a file related to the threat was indeed found.
A proven, reliable antivirus solution is an important network security tool that you need on your network, but in today’s virulent, ever-changing threat landscape, it by no means provides the comprehensive protection you need. There is no substitute for comprehensive monitoring by a SIEM with a wealth of built-in knowledge about cryptic security logs and intelligent, pre-built rules to catch unusual activity.

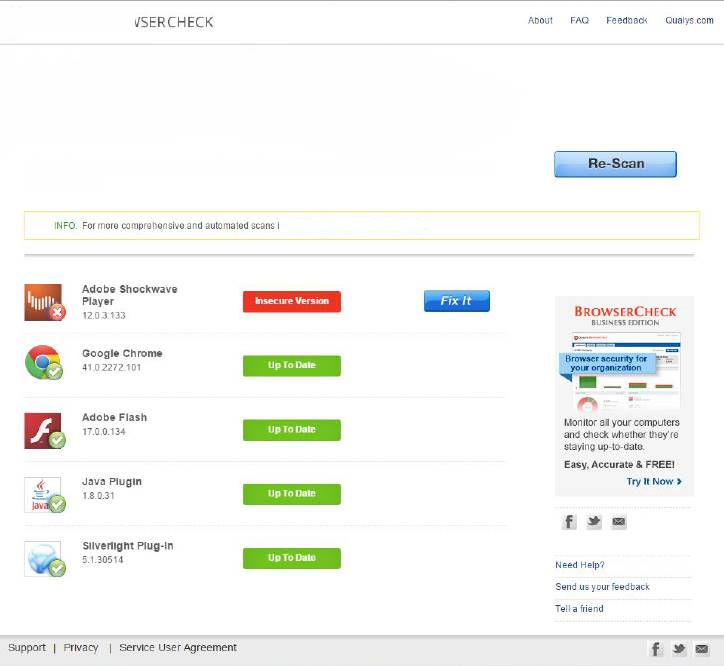
Adobe Flash was suspected as the malware’s entry point because Shockwave was found to be improperly patched during a patch-scanning assessment of the computer. (Figure 2) Unusual, irregular browser helper objects were also found; this situation is common when malware wants to hijack and redirect a browser session or send a user to a malicious site.
THE HACK IDENTIFIED
The organization used LogRhythm to initiate a full packet capture and deep packet inspection (DPI) of all traffic initiated during tests on the computer. A common destination IP address was found that did not belong to the organization. Naturally, this address raised suspicions: All traffic from the isolated laptop was going to the same IP address (which did not belong to the organization), indicating a possible hidden proxy mechanism on the isolated computer. See Figure 3.

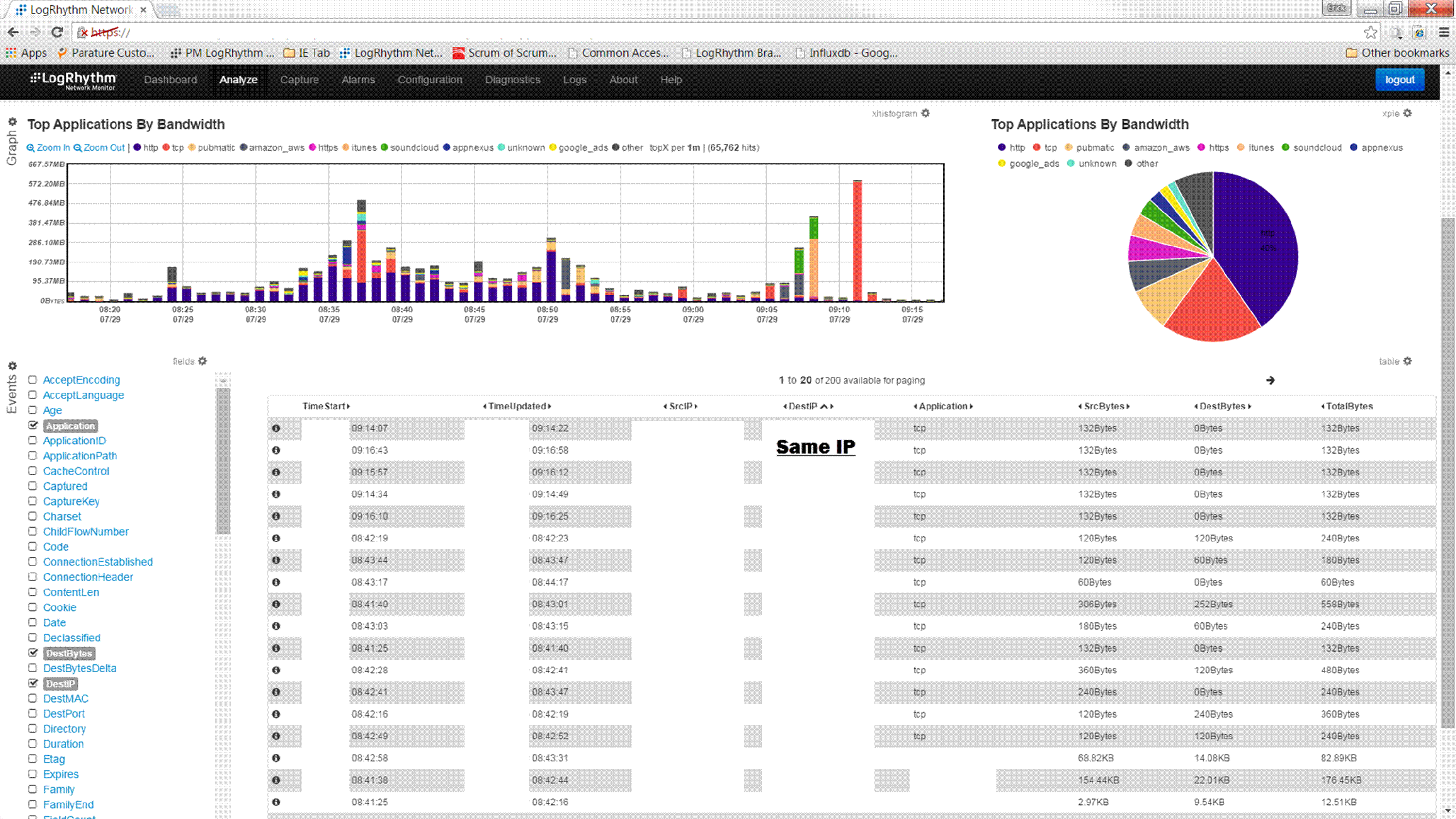
Figure 3: A DPI showed traffic consistently going to the same IP address
Running ipconfig/displaydns showed that all traffic from the computer resolved to a common host record. Obviously, this was a glaring red-flag. Because the computer was sending every outbound packet to the same IP address, the problem was identified as intentional DNS poisoning.
It was important to the SOC to find out where the traffic was headed. Studying the IP address itself, the team identified a proxy IP address (DHCP lease) from an ISP in the United States. The SOC then contacted the ISP, which confirmed that the server was a compromised computer on its watch list.
The ISP then notified its customer (who had no malicious intent) that their server was hosting a compromised node (which was redirecting traffic to a location in Finland). The customer then took the server off the network and got the situation resolved.
Cybercriminals had been capturing and redirecting traffic through illegally compromised systems and would have had many opportunities to do harm, but they were thwarted in this case.
THE HACK DISRUPTED
The investigation team uploaded the suspicious files to the antivirus community for the purpose of building awareness and with the hope that the community could create and deploy signatures and other heuristics to combat the malware threat.
Finally, to help prevent the same problem from happening again, the organization used LogRhythm to create a DPI rule to flag, alert, and capture proxy traffic and the same malware, should it reappear. (Figure 4) The computer that experienced the suspicious activity was reimaged, and patching was tightened on it and on computers across the company for potential Flash- and Shockwave-related problems for even greater risk mitigation.
Figure 4: A DPI rule monitors for traffic sent to the malicious IP address
None of the organization’s vital information was compromised, because the suspicious activity was caught so quickly and aggressively, and because effective action was taken so promptly. What could have been a major incident, or even a catastrophic data breach, was a mere bump in the road.
CONCLUSION
Malicious external attackers will use any means to access corporate information. Delivery mechanisms such as phishing-based attachments and malware-laden websites allow attackers to enter the figurative four walls of your organization. Unpatched applications such as Flash and Java allow access to credentials, the underlying operating system, data, and applications, giving the external attacker the ability to not just access corporate data but, as in the case of the scenario above, the ability to pass any obtained information outside the corporate walls for further malicious use. It all starts with one compromised endpoint.
Organizations can no longer rely simply on signature-based scanning of machines to identify malware. Polymorphic malware takes on an infinite number of forms, making it difficult to identify. And malware doesn’t exist for the sake of just existing; it has a purpose in mind that always involves taking something from you. So, a comprehensive approach to protecting your organization will entail not just looking at malware as a set of files to be detected, but also looking at it in terms of the actions it takes. You should be looking for ways to detect those actions on your network with the same determination with which you’d use an antivirus scanner to look for malware executables.
By taking this approach to thwarting malware, LogRhythm’s customer was able to automatically identify and address a potential issue the moment it arose, well before any damage could be done. Expanding your anti-malware efforts beyond simple machine scans to include scanning the network for malware activity will create a layered defense, ensuring the greatest effort in stopping malware in its tracks.
ABOUT Logrhythm
LogRhythm, a leader in security intelligence and analytics, empowers organizations around the globe to rapidly detect, respond to and neutralize damaging cyber threats. The company’s award-winning platform unifies next-generation SIEM, log management, network and endpoint monitoring and forensics, and security analytics. In addition to protecting customers from the risks associated with cyber threats, LogRhythm provides innovative compliance automation and assurance, and enhanced IT intelligence.
Consistently recognized by third-party experts, LogRhythm has been positioned as a Leader in Gartner’s SIEM Magic Quadrant report for four consecutive years, named a “Champion” in Info-Tech Research Group’s 2014-15 SIEM Vendor Landscape report and ranked Best-in-Class (No. 1) in DCIG’s 2014-15 SIEM Appliance Buyer’s Guide, awarded the SANS Institute's "Best of 2014" award in SIEM and received the SC Magazine Reader Trust Award for "Best SIEM Solution" in April 2015. Additionally, the company earned Frost & Sullivan’s SIEM/LM Global Market Penetration Leadership Award and been named a Top Workplace by the Denver Post. LogRhythm is headquartered in Boulder, Colorado, with operations throughout North and South America, Europe and the Asia Pacific region. www.logrhythm.com
[i] IDC,
The Link Between Pirated Software and Cybersecurity Breaches
(2014)
[ii] Verizon,
Data Breach Investigations Report
(2015)
[iii] Ponemon,
State of the Endpoint Report: User-Centric Risk (2015)